参考资料:
https://wiki.openwrt.org/oldwiki/wpa2enterprise
暂时来说,EAP是起来了,但是还是没搞懂怎么用该死的sql来做储存。而且我根据教程用原版配置文件慢慢改出来的配置超他妈神奇的不能接受localhost的请求,偏偏来自其他机器的请求就能收到,真是理解不能。
废话不多说,直接开始:
1:替换掉原有的mini工具包,官方出场的固件自带的不支持EAP。如果没有openssl的话,也顺便装上。
opkg remove wpad-mini hostapd-mini opkg install wpad hostapd openssl-util
2:安装freeradius
opkg install freeradius2 freeradius2-common freeradius2-democerts freeradius2-mod-always freeradius2-m od-attr-filter freeradius2-mod-attr-rewrite freeradius2-mod-chap freeradius2-mod-detail freeradius2-mod-eap freeradiu s2-mod-eap-gtc freeradius2-mod-eap-md5 freeradius2-mod-eap-mschapv2 freeradius2-mod-eap-peap freeradius2-mod-eap-tls freeradius2-mod-eap-ttls freeradius2-mod-exec freeradius2-mod-expiration freeradius2-mod-expr freeradius2-mod-files f reeradius2-mod-ldap freeradius2-mod-logintime freeradius2-mod-mschap freeradius2-mod-pap freeradius2-mod-passwd freeradius2-mod-preprocess freeradiu s2-mod-radutmp freeradius2-mod-realm freeradius2-mod-sql freeradius2-mod-sql-mysql freeradius2-mod-sql-pgsql freeradi us2-mod-sql-sqlite freeradius2-mod-sqlcounter freeradius2-mod-sqllog freeradius2-utils
可以酌情减掉不需要的部分,这次主要用到的有chap eap-mschapv2 eap-tls files这几个。
3.把全部的配置文件备份起来包括/etc/freeradius2/下面的几个.conf还有sites里面的那个default,通通移到别的地方,因为完全不需要这么臃肿的配置文件(而且我试过用了反而连不上这种糟糕的状况)。然后创建下面几个配置文件
radiusd.conf
prefix = /usr
exec_prefix = /usr
sysconfdir = /etc
localstatedir = /var
sbindir = /usr/sbin
logdir = ${localstatedir}/log/radius
raddbdir = /etc/freeradius2
dictionary = /usr/share/freeradius2/
db_dir = ${raddbdir}/db
libdir = /usr/lib/freeradius2
radacctdir = ${logdir}/radacct
confdir = ${raddbdir}
run_dir = ${localstatedir}/run
listen {
ipaddr = *
port = 0
type = auth
}
thread pool {
start_servers = 1
max_servers = 4
min_spare_servers = 1
max_spare_servers = 3
max_requests_per_server = 0
}
$INCLUDE ${confdir}/clients.conf
modules {
mschap {
authtype = MS-CHAP
}
$INCLUDE ${confdir}/eap.conf
mschapv2 {
}
files {
usersfile = ${confdir}/users
compat = no
}
}
authorize {
files
mschap
eap
}
authenticate {
Auth-Type MS-CHAP {
mschap
}
eap
}
clients.conf
client 127.0.0.1 {
secret = thisisafuckingsecrectpasswordyoudontknow
shortname = localhost
nastype = other # localhost isn't usually a NAS...
}
eap.conf
eap {
default_eap_type = peap
timer_expire = 60
ignore_unknown_eap_types = no
cisco_accounting_username_bug = no
mschapv2 {
}
tls {
rsa_key_length = 2048
dh_key_length = 1024
private_key_password = whatever
private_key_file = ${raddbdir}/certs/radius.key
certificate_file = ${raddbdir}/certs/radius.crt
CA_file = ${raddbdir}/certs/radius.crt
dh_file = ${raddbdir}/certs/dh
fragment_size = 1024
}
peap {
default_eap_type = mschapv2
}
}
PS:记得创建证书和dh文件
openssl req -x509 -newkey rsa:2048 -keyout radius.key -out radius.crt -days 3650 openssl dhparam -out dh 1024
user
DEFAULT Group == "disabled", Auth-Type := Reject
Reply-Message = "Your account has been disabled."
fruser Cleartext-Password := "fruser"
Reply-Message = "Hello, %{User-Name}",
Fall-Through = no
PS:如果后面还有其他的用户,Fall-Through就用yes,否则用no
配置文件都写好之后,用 radiusd -XX 来检查服务器是否能够正常工作。如果没问题的话就下一步,如果有问题……自己google吧。
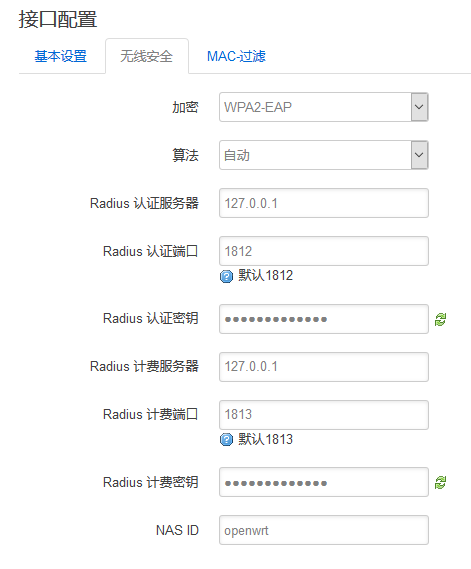
3:修改openwrt的无线设置,选择EAP作为加密方式,就像下面这样
保存并应用,搞定收工。