之前自己做了ec的key做csr的时候,startcom跟我说密钥长度太短,不给我用,现在看来是支持了。
ec的证书制作方法参见这个,现在startcom支持一个证书5个域名,基本上一个证书可以搞定。不过部署之后在ssllab检测的时候发现很多平台不支持,不知道为何,还真要认真的修整一下才行。
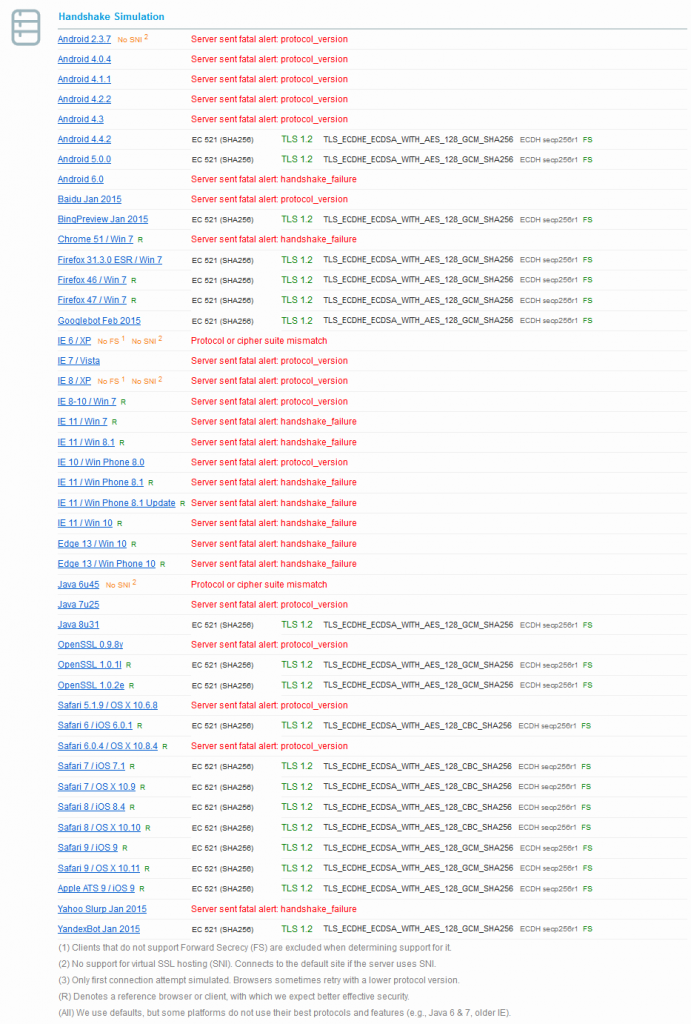 Chrome居然不支持,真是太让我吃惊了,IE系列基本上全跪,Android4.4.2和Android5都支持反而到了Android6又有问题,真是奇怪。
Chrome居然不支持,真是太让我吃惊了,IE系列基本上全跪,Android4.4.2和Android5都支持反而到了Android6又有问题,真是奇怪。
之前自己做了ec的key做csr的时候,startcom跟我说密钥长度太短,不给我用,现在看来是支持了。
ec的证书制作方法参见这个,现在startcom支持一个证书5个域名,基本上一个证书可以搞定。不过部署之后在ssllab检测的时候发现很多平台不支持,不知道为何,还真要认真的修整一下才行。
 Chrome居然不支持,真是太让我吃惊了,IE系列基本上全跪,Android4.4.2和Android5都支持反而到了Android6又有问题,真是奇怪。
Chrome居然不支持,真是太让我吃惊了,IE系列基本上全跪,Android4.4.2和Android5都支持反而到了Android6又有问题,真是奇怪。
听闻了除了RSA和DSA以外,出现了新的加密算法,ecc(椭圆曲线加密算法),于是打算来尝尝鲜。
openssl目前的版本已经支持ecc,可以直接升成ecc的密钥和签署ecc的证书。用法大概是这样:
root@vultr:/tmp# openssl ecparam help unknown option help ecparam [options] <infile >outfile where options are -inform arg input format - default PEM (DER or PEM) -outform arg output format - default PEM -in arg input file - default stdin -out arg output file - default stdout -noout do not print the ec parameter -text print the ec parameters in text form -check validate the ec parameters -C print a 'C' function creating the parameters -name arg use the ec parameters with 'short name' name -list_curves prints a list of all currently available curve 'short names' -conv_form arg specifies the point conversion form possible values: compressed uncompressed (default) hybrid -param_enc arg specifies the way the ec parameters are encoded in the asn1 der encoding possible values: named_curve (default) explicit -no_seed if 'explicit' parameters are chosen do not use the seed -genkey generate ec key -rand file files to use for random number input -engine e use engine e, possibly a hardware device
首先检查一下当前openssl支持的密钥长度
root@vultr:/tmp# openssl ecparam -list_curves secp112r1 : SECG/WTLS curve over a 112 bit prime field secp112r2 : SECG curve over a 112 bit prime field secp128r1 : SECG curve over a 128 bit prime field secp128r2 : SECG curve over a 128 bit prime field secp160k1 : SECG curve over a 160 bit prime field secp160r1 : SECG curve over a 160 bit prime field secp160r2 : SECG/WTLS curve over a 160 bit prime field secp192k1 : SECG curve over a 192 bit prime field secp224k1 : SECG curve over a 224 bit prime field secp224r1 : NIST/SECG curve over a 224 bit prime field secp256k1 : SECG curve over a 256 bit prime field secp384r1 : NIST/SECG curve over a 384 bit prime field secp521r1 : NIST/SECG curve over a 521 bit prime field prime192v1: NIST/X9.62/SECG curve over a 192 bit prime field prime192v2: X9.62 curve over a 192 bit prime field prime192v3: X9.62 curve over a 192 bit prime field prime239v1: X9.62 curve over a 239 bit prime field prime239v2: X9.62 curve over a 239 bit prime field prime239v3: X9.62 curve over a 239 bit prime field prime256v1: X9.62/SECG curve over a 256 bit prime field sect113r1 : SECG curve over a 113 bit binary field sect113r2 : SECG curve over a 113 bit binary field sect131r1 : SECG/WTLS curve over a 131 bit binary field sect131r2 : SECG curve over a 131 bit binary field sect163k1 : NIST/SECG/WTLS curve over a 163 bit binary field sect163r1 : SECG curve over a 163 bit binary field sect163r2 : NIST/SECG curve over a 163 bit binary field sect193r1 : SECG curve over a 193 bit binary field sect193r2 : SECG curve over a 193 bit binary field sect233k1 : NIST/SECG/WTLS curve over a 233 bit binary field sect233r1 : NIST/SECG/WTLS curve over a 233 bit binary field sect239k1 : SECG curve over a 239 bit binary field sect283k1 : NIST/SECG curve over a 283 bit binary field sect283r1 : NIST/SECG curve over a 283 bit binary field sect409k1 : NIST/SECG curve over a 409 bit binary field sect409r1 : NIST/SECG curve over a 409 bit binary field sect571k1 : NIST/SECG curve over a 571 bit binary field sect571r1 : NIST/SECG curve over a 571 bit binary field c2pnb163v1: X9.62 curve over a 163 bit binary field c2pnb163v2: X9.62 curve over a 163 bit binary field c2pnb163v3: X9.62 curve over a 163 bit binary field c2pnb176v1: X9.62 curve over a 176 bit binary field c2tnb191v1: X9.62 curve over a 191 bit binary field c2tnb191v2: X9.62 curve over a 191 bit binary field c2tnb191v3: X9.62 curve over a 191 bit binary field c2pnb208w1: X9.62 curve over a 208 bit binary field c2tnb239v1: X9.62 curve over a 239 bit binary field c2tnb239v2: X9.62 curve over a 239 bit binary field c2tnb239v3: X9.62 curve over a 239 bit binary field c2pnb272w1: X9.62 curve over a 272 bit binary field c2pnb304w1: X9.62 curve over a 304 bit binary field c2tnb359v1: X9.62 curve over a 359 bit binary field c2pnb368w1: X9.62 curve over a 368 bit binary field c2tnb431r1: X9.62 curve over a 431 bit binary field wap-wsg-idm-ecid-wtls1: WTLS curve over a 113 bit binary field wap-wsg-idm-ecid-wtls3: NIST/SECG/WTLS curve over a 163 bit binary field wap-wsg-idm-ecid-wtls4: SECG curve over a 113 bit binary field wap-wsg-idm-ecid-wtls5: X9.62 curve over a 163 bit binary field wap-wsg-idm-ecid-wtls6: SECG/WTLS curve over a 112 bit prime field wap-wsg-idm-ecid-wtls7: SECG/WTLS curve over a 160 bit prime field wap-wsg-idm-ecid-wtls8: WTLS curve over a 112 bit prime field wap-wsg-idm-ecid-wtls9: WTLS curve over a 160 bit prime field wap-wsg-idm-ecid-wtls10: NIST/SECG/WTLS curve over a 233 bit binary field wap-wsg-idm-ecid-wtls11: NIST/SECG/WTLS curve over a 233 bit binary field wap-wsg-idm-ecid-wtls12: WTLS curvs over a 224 bit prime field Oakley-EC2N-3: IPSec/IKE/Oakley curve #3 over a 155 bit binary field. Not suitable for ECDSA. Questionable extension field! Oakley-EC2N-4: IPSec/IKE/Oakley curve #4 over a 185 bit binary field. Not suitable for ECDSA. Questionable extension field!
然后就挑其中一个来制作ecc密钥
openssl ecparam -genkey -name prime256v1 -noout -out ecc.key
参数中的noout是指不输出ec参数,genkey是生成密钥。
ecc密钥生成之后,就可以按照老方法来生成证书了。先生成证书请求:
openssl req -new -key ecc.key -out ecc.csr
再对其进行签署,可以自签署,或者交给其他的CA进行签署,或者自己用自己的CA证书进行签署:
自签署:
openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt
自己用自己的CA证书进行签署:
openssl ca -cert ca.crt -extensions server_cert -days 375 -notext -md sha256 -in ecc.csr -out ecc.crt签署服务器证书用server_cert插件,签署客户端证书用usr_cert插件。
大功告成。