之前自己做了ec的key做csr的时候,startcom跟我说密钥长度太短,不给我用,现在看来是支持了。
ec的证书制作方法参见这个,现在startcom支持一个证书5个域名,基本上一个证书可以搞定。不过部署之后在ssllab检测的时候发现很多平台不支持,不知道为何,还真要认真的修整一下才行。
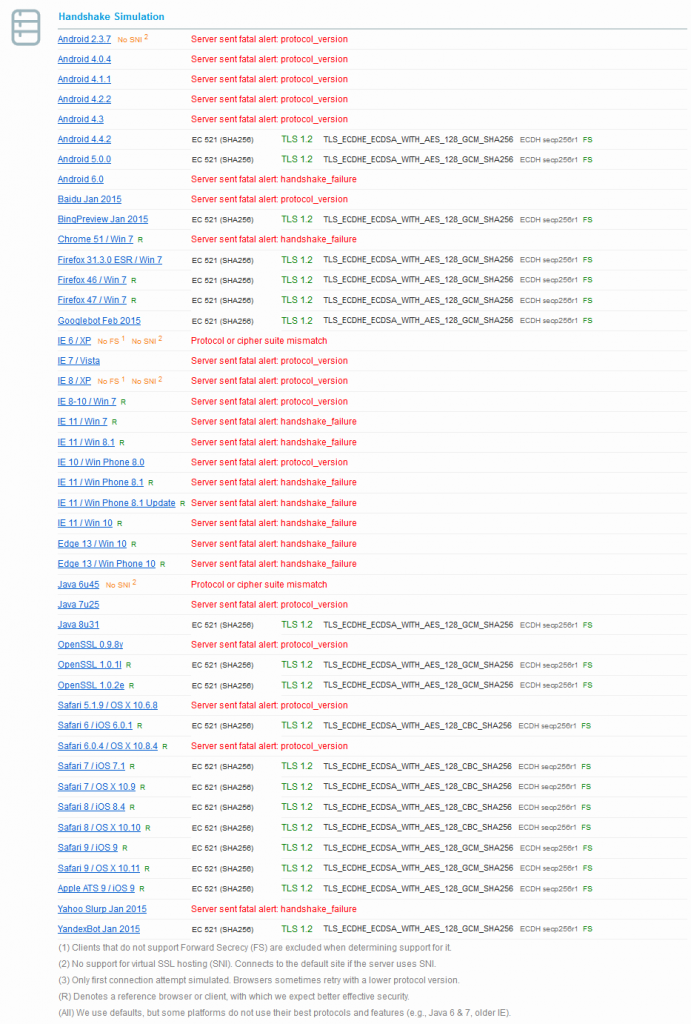 Chrome居然不支持,真是太让我吃惊了,IE系列基本上全跪,Android4.4.2和Android5都支持反而到了Android6又有问题,真是奇怪。
Chrome居然不支持,真是太让我吃惊了,IE系列基本上全跪,Android4.4.2和Android5都支持反而到了Android6又有问题,真是奇怪。
之前自己做了ec的key做csr的时候,startcom跟我说密钥长度太短,不给我用,现在看来是支持了。
ec的证书制作方法参见这个,现在startcom支持一个证书5个域名,基本上一个证书可以搞定。不过部署之后在ssllab检测的时候发现很多平台不支持,不知道为何,还真要认真的修整一下才行。
 Chrome居然不支持,真是太让我吃惊了,IE系列基本上全跪,Android4.4.2和Android5都支持反而到了Android6又有问题,真是奇怪。
Chrome居然不支持,真是太让我吃惊了,IE系列基本上全跪,Android4.4.2和Android5都支持反而到了Android6又有问题,真是奇怪。
听闻了除了RSA和DSA以外,出现了新的加密算法,ecc(椭圆曲线加密算法),于是打算来尝尝鲜。
openssl目前的版本已经支持ecc,可以直接升成ecc的密钥和签署ecc的证书。用法大概是这样:
root@vultr:/tmp# openssl ecparam help unknown option help ecparam [options] <infile >outfile where options are -inform arg input format - default PEM (DER or PEM) -outform arg output format - default PEM -in arg input file - default stdin -out arg output file - default stdout -noout do not print the ec parameter -text print the ec parameters in text form -check validate the ec parameters -C print a 'C' function creating the parameters -name arg use the ec parameters with 'short name' name -list_curves prints a list of all currently available curve 'short names' -conv_form arg specifies the point conversion form possible values: compressed uncompressed (default) hybrid -param_enc arg specifies the way the ec parameters are encoded in the asn1 der encoding possible values: named_curve (default) explicit -no_seed if 'explicit' parameters are chosen do not use the seed -genkey generate ec key -rand file files to use for random number input -engine e use engine e, possibly a hardware device
首先检查一下当前openssl支持的密钥长度
root@vultr:/tmp# openssl ecparam -list_curves secp112r1 : SECG/WTLS curve over a 112 bit prime field secp112r2 : SECG curve over a 112 bit prime field secp128r1 : SECG curve over a 128 bit prime field secp128r2 : SECG curve over a 128 bit prime field secp160k1 : SECG curve over a 160 bit prime field secp160r1 : SECG curve over a 160 bit prime field secp160r2 : SECG/WTLS curve over a 160 bit prime field secp192k1 : SECG curve over a 192 bit prime field secp224k1 : SECG curve over a 224 bit prime field secp224r1 : NIST/SECG curve over a 224 bit prime field secp256k1 : SECG curve over a 256 bit prime field secp384r1 : NIST/SECG curve over a 384 bit prime field secp521r1 : NIST/SECG curve over a 521 bit prime field prime192v1: NIST/X9.62/SECG curve over a 192 bit prime field prime192v2: X9.62 curve over a 192 bit prime field prime192v3: X9.62 curve over a 192 bit prime field prime239v1: X9.62 curve over a 239 bit prime field prime239v2: X9.62 curve over a 239 bit prime field prime239v3: X9.62 curve over a 239 bit prime field prime256v1: X9.62/SECG curve over a 256 bit prime field sect113r1 : SECG curve over a 113 bit binary field sect113r2 : SECG curve over a 113 bit binary field sect131r1 : SECG/WTLS curve over a 131 bit binary field sect131r2 : SECG curve over a 131 bit binary field sect163k1 : NIST/SECG/WTLS curve over a 163 bit binary field sect163r1 : SECG curve over a 163 bit binary field sect163r2 : NIST/SECG curve over a 163 bit binary field sect193r1 : SECG curve over a 193 bit binary field sect193r2 : SECG curve over a 193 bit binary field sect233k1 : NIST/SECG/WTLS curve over a 233 bit binary field sect233r1 : NIST/SECG/WTLS curve over a 233 bit binary field sect239k1 : SECG curve over a 239 bit binary field sect283k1 : NIST/SECG curve over a 283 bit binary field sect283r1 : NIST/SECG curve over a 283 bit binary field sect409k1 : NIST/SECG curve over a 409 bit binary field sect409r1 : NIST/SECG curve over a 409 bit binary field sect571k1 : NIST/SECG curve over a 571 bit binary field sect571r1 : NIST/SECG curve over a 571 bit binary field c2pnb163v1: X9.62 curve over a 163 bit binary field c2pnb163v2: X9.62 curve over a 163 bit binary field c2pnb163v3: X9.62 curve over a 163 bit binary field c2pnb176v1: X9.62 curve over a 176 bit binary field c2tnb191v1: X9.62 curve over a 191 bit binary field c2tnb191v2: X9.62 curve over a 191 bit binary field c2tnb191v3: X9.62 curve over a 191 bit binary field c2pnb208w1: X9.62 curve over a 208 bit binary field c2tnb239v1: X9.62 curve over a 239 bit binary field c2tnb239v2: X9.62 curve over a 239 bit binary field c2tnb239v3: X9.62 curve over a 239 bit binary field c2pnb272w1: X9.62 curve over a 272 bit binary field c2pnb304w1: X9.62 curve over a 304 bit binary field c2tnb359v1: X9.62 curve over a 359 bit binary field c2pnb368w1: X9.62 curve over a 368 bit binary field c2tnb431r1: X9.62 curve over a 431 bit binary field wap-wsg-idm-ecid-wtls1: WTLS curve over a 113 bit binary field wap-wsg-idm-ecid-wtls3: NIST/SECG/WTLS curve over a 163 bit binary field wap-wsg-idm-ecid-wtls4: SECG curve over a 113 bit binary field wap-wsg-idm-ecid-wtls5: X9.62 curve over a 163 bit binary field wap-wsg-idm-ecid-wtls6: SECG/WTLS curve over a 112 bit prime field wap-wsg-idm-ecid-wtls7: SECG/WTLS curve over a 160 bit prime field wap-wsg-idm-ecid-wtls8: WTLS curve over a 112 bit prime field wap-wsg-idm-ecid-wtls9: WTLS curve over a 160 bit prime field wap-wsg-idm-ecid-wtls10: NIST/SECG/WTLS curve over a 233 bit binary field wap-wsg-idm-ecid-wtls11: NIST/SECG/WTLS curve over a 233 bit binary field wap-wsg-idm-ecid-wtls12: WTLS curvs over a 224 bit prime field Oakley-EC2N-3: IPSec/IKE/Oakley curve #3 over a 155 bit binary field. Not suitable for ECDSA. Questionable extension field! Oakley-EC2N-4: IPSec/IKE/Oakley curve #4 over a 185 bit binary field. Not suitable for ECDSA. Questionable extension field!
然后就挑其中一个来制作ecc密钥
openssl ecparam -genkey -name prime256v1 -noout -out ecc.key
参数中的noout是指不输出ec参数,genkey是生成密钥。
ecc密钥生成之后,就可以按照老方法来生成证书了。先生成证书请求:
openssl req -new -key ecc.key -out ecc.csr
再对其进行签署,可以自签署,或者交给其他的CA进行签署,或者自己用自己的CA证书进行签署:
自签署:
openssl x509 -req -days 365 -in server.csr -signkey server.key -out server.crt
自己用自己的CA证书进行签署:
openssl ca -cert ca.crt -extensions server_cert -days 375 -notext -md sha256 -in ecc.csr -out ecc.crt签署服务器证书用server_cert插件,签署客户端证书用usr_cert插件。
大功告成。
现在dns污染真的很烦人,总是会莫名其妙地遇到然后导致访问失败,折腾了相当久都没有什么好办法。dnsmasq上加上了chinalist,可以搞定国内的大部分域名,大部分CDN也能用,但是国外的地址解析一直都不是很稳定。
试过直接经梯子用国外的dns服务器,但是由于梯子本身的不稳定,上网的体验太差了,动不动就解析不了ip地址。然后经过一番搜索,得知了dnscrypt已经移植到了openwrt上,于是果断已看,还真有。
root@Belkin ~ # opkg list | grep dnscrypt dnscrypt-proxy - 1.4.3-1 - dnscrypt-proxy provides local service which can be used directly as your local resolver or as a DNS forwarder, encrypting and authenticating requests using the DNSCrypt protocol and passing them to an upstream server. The DNSCrypt protocol uses high-speed high-security elliptic-curve cryptography and is very similar to DNSCurve, but focuses on securing communications between a client and its first-level resolver.
结果装上之后一试,哎呦,速度还可以,也比较稳定,没出现什么经常性的抽风。
安装的过程非常简单,opkg install dnscrypt-proxy之后修改/etc/config/dnscrypt-proxy,只需要取消注释一行就可以用了
config dnscrypt-proxy
option address '127.0.0.1'
option port '5353'
option resolver 'cisco'
# option resolvers_list '/usr/share/dnscrypt-proxy/dnscrypt-resolvers.csv'
# option ephemeral_keys '1'至于可以用的公用解析器,可以参考public DNSCrypt resolvers。
dig了一下,查询时间大概在200-ms,效果良好~
root@Belkin /etc/config # dig youtube.com -p 5353 127.0.0.1 ; <<>> DiG 9.9.8-P3 <<>> youtube.com -p 5353 127.0.0.1 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 40410 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;youtube.com. IN A ;; ANSWER SECTION: youtube.com. 300 IN A 216.58.203.14 ;; Query time: 194 msec ;; SERVER: 127.0.0.1#5353(127.0.0.1) ;; WHEN: Thu Jun 30 23:51:44 CST 2016 ;; MSG SIZE rcvd: 56 ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NXDOMAIN, id: 6494 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 1, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;127.0.0.1. IN A ;; AUTHORITY SECTION: . 2158 IN SOA a.root-servers.net. nstld.verisign-grs.com. 2016062901 1800 900 604800 86400 ;; Query time: 188 msec ;; SERVER: 127.0.0.1#5353(127.0.0.1) ;; WHEN: Thu Jun 30 23:51:44 CST 2016 ;; MSG SIZE rcvd: 113
然后配置dnsmasq,修改/etc/dnsmasq.conf,添加一行
conf-dir=/etc/dnsmasq.d
然后把https://raw.githubusercontent.com/felixonmars/dnsmasq-china-list/master/accelerated-domains.china.conf下载到/etc/dnsmasq.d/,再去修改dnsmasq的转发为127.0.0.1#5353
或者直接修改/etc/config/dhcp
config dnsmasq
option domainneeded '1'
option boguspriv '1'
option localise_queries '1'
option local '/lan/'
option domain 'lan'
option expandhosts '1'
option authoritative '1'
option readethers '1'
option leasefile '/tmp/dhcp.leases'
option resolvfile '/tmp/resolv.conf.auto'
option rebind_protection '0'
list server '127.0.0.1#5353'
原文:https://support.google.com/a/answer/60764?hl=zh-Hans
Google有着巨量的ip地址,并提供了一个统一的查询方式来查询当前Google所提供服务的所有ip block。
nslookup -q=TXT _spf.google.com 8.8.8.8
此操作会返回一张列表,其中列出了Google SPF记录中包含的网域,例如:
_netblocks.google.com、_netblocks2.google.com、_netblocks3.google.com
现在,请逐个查找与这些网域关联的DNS记录,例如:
nslookup -q=TXT _netblocks.google.com 8.8.8.8 nslookup -q=TXT _netblocks2.google.com 8.8.8.8 nslookup -q=TXT _netblocks3.google.com 8.8.8.8
这些命令得到的结果中会包含当前地址范围。
根据注释,这并不是所有Google服务器的ip,不过看起来也差不远了。
参考资料:
https://wiki.openwrt.org/oldwiki/wpa2enterprise
暂时来说,EAP是起来了,但是还是没搞懂怎么用该死的sql来做储存。而且我根据教程用原版配置文件慢慢改出来的配置超他妈神奇的不能接受localhost的请求,偏偏来自其他机器的请求就能收到,真是理解不能。
废话不多说,直接开始:
1:替换掉原有的mini工具包,官方出场的固件自带的不支持EAP。如果没有openssl的话,也顺便装上。
opkg remove wpad-mini hostapd-mini opkg install wpad hostapd openssl-util
2:安装freeradius
opkg install freeradius2 freeradius2-common freeradius2-democerts freeradius2-mod-always freeradius2-m od-attr-filter freeradius2-mod-attr-rewrite freeradius2-mod-chap freeradius2-mod-detail freeradius2-mod-eap freeradiu s2-mod-eap-gtc freeradius2-mod-eap-md5 freeradius2-mod-eap-mschapv2 freeradius2-mod-eap-peap freeradius2-mod-eap-tls freeradius2-mod-eap-ttls freeradius2-mod-exec freeradius2-mod-expiration freeradius2-mod-expr freeradius2-mod-files f reeradius2-mod-ldap freeradius2-mod-logintime freeradius2-mod-mschap freeradius2-mod-pap freeradius2-mod-passwd freeradius2-mod-preprocess freeradiu s2-mod-radutmp freeradius2-mod-realm freeradius2-mod-sql freeradius2-mod-sql-mysql freeradius2-mod-sql-pgsql freeradi us2-mod-sql-sqlite freeradius2-mod-sqlcounter freeradius2-mod-sqllog freeradius2-utils
可以酌情减掉不需要的部分,这次主要用到的有chap eap-mschapv2 eap-tls files这几个。
3.把全部的配置文件备份起来包括/etc/freeradius2/下面的几个.conf还有sites里面的那个default,通通移到别的地方,因为完全不需要这么臃肿的配置文件(而且我试过用了反而连不上这种糟糕的状况)。然后创建下面几个配置文件
radiusd.conf
prefix = /usr
exec_prefix = /usr
sysconfdir = /etc
localstatedir = /var
sbindir = /usr/sbin
logdir = ${localstatedir}/log/radius
raddbdir = /etc/freeradius2
dictionary = /usr/share/freeradius2/
db_dir = ${raddbdir}/db
libdir = /usr/lib/freeradius2
radacctdir = ${logdir}/radacct
confdir = ${raddbdir}
run_dir = ${localstatedir}/run
listen {
ipaddr = *
port = 0
type = auth
}
thread pool {
start_servers = 1
max_servers = 4
min_spare_servers = 1
max_spare_servers = 3
max_requests_per_server = 0
}
$INCLUDE ${confdir}/clients.conf
modules {
mschap {
authtype = MS-CHAP
}
$INCLUDE ${confdir}/eap.conf
mschapv2 {
}
files {
usersfile = ${confdir}/users
compat = no
}
}
authorize {
files
mschap
eap
}
authenticate {
Auth-Type MS-CHAP {
mschap
}
eap
}
clients.conf
client 127.0.0.1 {
secret = thisisafuckingsecrectpasswordyoudontknow
shortname = localhost
nastype = other # localhost isn't usually a NAS...
}
eap.conf
eap {
default_eap_type = peap
timer_expire = 60
ignore_unknown_eap_types = no
cisco_accounting_username_bug = no
mschapv2 {
}
tls {
rsa_key_length = 2048
dh_key_length = 1024
private_key_password = whatever
private_key_file = ${raddbdir}/certs/radius.key
certificate_file = ${raddbdir}/certs/radius.crt
CA_file = ${raddbdir}/certs/radius.crt
dh_file = ${raddbdir}/certs/dh
fragment_size = 1024
}
peap {
default_eap_type = mschapv2
}
}
PS:记得创建证书和dh文件
openssl req -x509 -newkey rsa:2048 -keyout radius.key -out radius.crt -days 3650 openssl dhparam -out dh 1024
user
DEFAULT Group == "disabled", Auth-Type := Reject
Reply-Message = "Your account has been disabled."
fruser Cleartext-Password := "fruser"
Reply-Message = "Hello, %{User-Name}",
Fall-Through = noPS:如果后面还有其他的用户,Fall-Through就用yes,否则用no
配置文件都写好之后,用 radiusd -XX 来检查服务器是否能够正常工作。如果没问题的话就下一步,如果有问题……自己google吧。
3:修改openwrt的无线设置,选择EAP作为加密方式,就像下面这样
保存并应用,搞定收工。
参考:https://wiki.openwrt.org/doc/howto/tftp.pxe-server
刚才把那台10年历史的老电脑翻了出来,着磨着这烂XP也该换掉了,想了想,打算换成debian,由于懒得做安装盘于是果断选择走PXE,大概是因为后来主板换过了,居然支持PXE启动,好了。着手安装。
看了一下debian的安装wiki,教程里面自带一份pxelinux.cfg/default的配置文件,但是我不想覆盖掉之前的版本,于是展开了看一下
debian-installer/i386/boot-screens/menu.cfg
这个文件,里面指向了四个文件
include debian-installer/i386/boot-screens/adtxt.cfg include debian-installer/i386/boot-screens/amdadtxt.cfg include debian-installer/i386/boot-screens/adgtk.cfg include debian-installer/i386/boot-screens/amdadgtk.cfg
于是在adtxt.cfg里面找到了kernel和append字段
kernel debian-installer/i386/linux append priority=low vga=788 initrd=debian-installer/i386/initrd.gz --- include debian-installer/i386/boot-screens/rqtxt.cfg
果断的选择将这俩字段添加到之前的default里面,然后net installer就跑起来了。没有nfs服务器出场的机会呢。
参考:http://unix.stackexchange.com/questions/61567/sshfs-specify-key
我记得似乎是写过这篇文,莫非是丢了?
使用方法:
sshfs [email protected]:/remote/path /local/path/ -o IdentityFile=/path/to/keymark一下。
前几天我在AWS的竞价请求莫名出问题了,我设定的价格是0.02每小时,在我查询当前价格的时候看到的也是0.003没小时,但是AWS却告诉我说价格超出设定值,实例被暂停了。然后我重新提交了一个一模一样的申请,结果却能顺利运行。
我提交了工单,但是3天没人理,优先级是低,这是我见过最糟糕的支持工单了。
想想前几个月忘记了AWS的流量政策结果在上面跑了个吃流量的货结果导致当月消费178刀,简直酸爽的难以置信。
得出来的结论就是,AWS这东西,穷人玩不起。
然后我又滚出AWS,跑到vultr去了。结果又丢了几篇文章。